The latest SY0-601 dumps are the best exam material for the “CompTIA Security+” 2023 certification exam.
leads4pass provides 965 latest exam questions and answers, download with PDF and VCE SY0-601 dumps: https://www.leads4pass.com/sy0-601.html, practice the latest exam questions to help candidates pass the exam successfully.
Not only that, participate in the SY0-601 online practice test to verify your current strength and help you further improve yourself.
Practice the latest SY0-601 exam questions online
| From | Number of exam questions | Exam name | Exam code | Answers |
| leads4pass | 15 | CompTIA Security+ | SY0-601 | View |
Question 1:
A company\’s bank has reported that multiple corporate credit cards have been stolen over the past several weeks. The bank has provided the names of the affected cardholders to the company\’s forensics team to assist in the cyber-incident investigation.
An incident responder learns the following information:
The timeline of stolen card numbers corresponds closely with affected users making Internet-based purchases from diverse websites via enterprise desktop PCs.
All purchase connections were encrypted, and the company uses an SSL inspection proxy for the inspection of encrypted traffic of the hardwired network.
Purchases made with corporate cards over the corporate guest WiFi network, where no SSL inspection occurs, were unaffected.
Which of the following is the MOST likely root cause?
A. HTTPS sessions are being downgraded to insecure cipher suites
B. The SSL inspection proxy is feeding events to a compromised SIEM
C. The payment providers are insecurely processing credit card charges
D. The adversary has not yet established a presence on the guest WiFi network
The purchases are only getting affected from systems where SSL inspection is occurring. It’s fine on all others. IT cant be an HTTPS downgrade as that wouldn’t be specific to the SSL inspection.
Question 2:
Which of the following would produce the closest experience of responding to an actual incident response scenario?
A. Lessons learned
B. Simulation
C. Walk-through
D. Tabletop
Question 3:
During a trial, a judge determined evidence gathered from a hard drive was not admissible. Which of the following BEST explains this reasoning?
A. The forensic investigator forgot to run a checksum on the disk image after the creation
B. The chain of custody form did not note time zone offsets between transportation regions
C. The computer was turned off. and a RAM image could not be taken at the same time D. The hard drive was not properly kept in an antistatic bag when it was moved
The question states that a trial Judge determined evidence gathered from a hard drive was not admissible. It is obvious that this is a legal matter. All of the remaining answers are of a technical nature, So consequently the only issue that a Judge can rule on is a Chain of custody issue. So, ladies and gentlemen, I rest my case (quickly bangs a gavel upon the desk)
Question 4:
A security analyst is reviewing logs on a server and observes the following output:
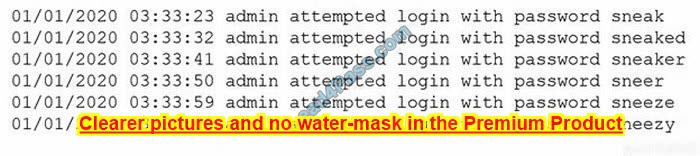
Which of the following is the security analyst observing?
A. A rainbow table attack
B. A password-spraying attack
C. A dictionary attack
D. A keylogger attack
predefined list of words = dictionary attack
Reference: https://www.imperva.com/learn/application-security/brute-force-attack/
Question 5:
A network administrator at a large organization is reviewing methods to improve the security of the wired LAN. Any security improvement must be centrally managed and allow corporate-owned devices to have access to the intranet but limit others to Internet access only. Which of the following should the administrator recommend?
A. 802.1X utilizing the current PKI infrastructure
B. SSO to authenticate corporate users
C. MAC address filtering with ACLs on the router D. PAM for user account management
It\’s possible to combine an 802.1x server with other network elements such as a virtual local area network (VLAN). For example, imagine you want to provide visitors with Internet access but prevent them from accessing internal network resources. You can configure the 802.1x server to grant full access to authorized clients but redirect unauthorized clients to a guest area of the network via a VLAN.
Question 6:
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a reek of this practice?
A. Default system configuration
B. Unsecure Protocols
C. Lack of vendor support
D. Weak encryption
Question 7:
The Chief Information Security Officer wants to prevent the exfiltration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the BEST solution to Implement?
A. DLP
B. USB data blocker
C. USB OTG
D. Disabling USB ports
The best solution to prevent the exfiltration of sensitive information from employee cell phones when using public USB power charging stations would be to use a USB data blocker. A USB data blocker is a device that can be used to physically block the data pins on a USB cable, preventing data transfer while still allowing the device to be charged. This would prevent employees from accidentally or maliciously transferring sensitive data from their cell phones to the public charging station. Options A, C, and D would not be effective in preventing this type of data exfiltration
Question 8:
Which of the following is MOST likely to contain ranked and ordered information on the likelihood and potential impact of catastrophic events that may affect business processes and systems, while also highlighting the residual risks that need to be managed after mitigating controls have been implemented?
A. An RTO report
B. A risk register
C. A business impact analysis
D. An asset value register
E. A disaster recovery plan
A risk register is a document that records all of your organization \’s identified risks, the likelihood and consequences of a risk occurring, the actions you are taking to reduce those risks, and who is responsible for managing them
Question 9:
A security analyst is receiving several alerts per user and is trying to determine If various logins are malicious. The security analyst would like to create a baseline of normal operations and reduce noise. Which of the following actions should the security analyst perform?
A. Adjust the data flow from authentication sources to the SIEM.
B. Disable email alerting and review the SIEM directly.
C. Adjust the sensitivity levels of the SIEM correlation engine.
D. Utilize behavioral analysis to enable the SIEM\’s learning mode.
Utilize behavioral analysis to enable the SIEM\’s learning mode.
UBA or User Behavior Analytics is a threat detection analysis technology that uses AI to understand how users normally behave and then find anomalous activities, which deviate from their normal behavior and may be indicative of a threat.
For this scenario, the SIEM will first learn what is normal behavior then when a baseline is created, it will know if any of the logins are malicious. Likely determined by when and where the logins are occurring and if it\’s different from the baseline. This should hopefully reduce the number of alerts occurring.
Question 10:
A security engineer needs to implement an MDM solution that complies with the corporate mobile device policy. The policy states that in order for mobile users to access corporate resources on their devices, the following requirements must be met:
1.
Mobile device OSs must be patched up to the latest release.
2.
A screen lock must be enabled (passcode or biometric).
3.
Corporate data must be removed if the device is reported lost or stolen.
Which of the following controls should the security engineer configure? (Choose two.)
A. Containerization
B. Storage segmentation
C. Posturing
D. Remote wipe
E. Full-device encryption
F. Geofencing
Question 11:
A university with remote campuses, which all use different service providers, loses Internet connectivity across all locations. After a few minutes, Internet and VoIP services are restored, only to go offline again at random intervals, typically within four minutes of services being restored. Outages continue throughout the day, impacting all inbound and outbound connections and services. Services that are limited to the local LAN or WiFi network are not impacted, but all WAN and VoIP services are affected.
Later that day, the edge-router manufacturer releases a CVE outlining the ability of an attacker to exploit the SIP protocol handling on devices, leading to resource exhaustion and system reloads.
Which of the following BEST describes this type of attack? (Choose two.)
A. DoS
B. SSL stripping
C. Memory leak
D. Race condition
E. Shimming
F. Refactoring
A DoS attack is a type of cyber attack that is designed to disrupt the availability of a network, system, or service. In this case, the attacker is using the exploit outlined in the CVE to disrupt the availability of Internet and VoIP services at the university\’s remote campuses.
A Memory Leak is a type of software bug that occurs when a program or application allocates memory for a task but fails to release the memory when it is no longer needed. This can lead to a depletion of available memory resources, causing the system to crash or become unstable. The fact that the outages at the university are occurring at random intervals and are being caused by system reloads suggests that a Memory Leak may be present.
Question 12:
The new Chief Executive Officer (CEO) of a large company has announced a partnership with a vendor that will provide multiple collaboration applications t make remote work easier. The company has a geographically dispersed staff located in numerous remote offices in different countries. The company\’s IT administrators are concerned about network traffic and load if all users simultaneously download the application.
Which of the following would work BEST to allow each geographic region to download the software without negatively impacting the corporate network?
A. Update the host IDS rules.
B. Enable application whitelisting.
C. Modify the corporate firewall rules.
D. Deploy all applications simultaneously.
Question 13:
The website http://companywebsite.com requires users to provide personal information, including security question responses, for registration. Which of the following would MOST likely cause a data breach?
A. Lack of input validation
B. Open permissions
C. Unsecure protocol
D. Missing patches
Website is using HTTP which is the unsecured protocol of HTTP
Question 14:
An organization is planning to open other data centers to sustain operations in the event of a natural disaster. Which of the following considerations would BEST support the organization\’s resiliency?
A. Geographic dispersal
B. Generator power
C. Fire suppression
D. Facility Automation
Placing that data center far away, maybe in another country can help protect against disasters like an earthquake
Question 15:
The Chief Security Officer (CSO) at a major hospital wants to implement SSO to help improve in the environment of patient data, particularly at shared terminals. The Chief Risk Officer (CRO) is concerned that training and guidance have been provided to frontline staff, and risk analysis has not been performed. Which of the following is the MOST likely cause of CRO\’s concerns?
A. SSO would simplify username and password management, making it easier for hackers to pass guess accounts.
B. SSO would reduce password fatigue, but staff would still need to remember more complex passwords.
C. SSO would reduce the password complexity for frontline staff.
D. SSO would reduce the resilience and availability of the system if the provider goes offline.
SSO works based upon a trust relationship set up between an application, known as the service provider, and an identity provider, like OneLogin. This trust relationship is often based upon a certificate that is exchanged between the identity provider and the service provider. This certificate can be used to sign identity information that is being sent from the identity provider to the service provider so that the service provider knows it is coming from a trusted source. In SSO, this identity data takes the form of tokens which contain identifying bits of information about the user like a user\’s email address or username.
…
Verify answer:
| Questions: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | B | B | B | C | A | B | B | B | D | AD | AC | B | C | A | D |
The above 15 latest SY0-601 exam questions and answers are shared for free. This is just to help candidates verify their current strengths.
Download the complete SY0-601 exam materials: https://www.leads4pass.com/sy0-601.html, Help you simulate exercises more easily.
Summarize:
The “CompTIA Security+ 2023” certification exam remains one of the most popular CompTIA certifications, so taking and passing it is something to celebrate, and we can imagine success in helping ourselves with Career prospects and the joy of increasing income.
Download SY0-601 dumps with the best materials of 2023: https://www.leads4pass.com/sy0-601.html, and practice the latest and complete SY0-601 exam questions to help you pass the exam.




